![]() This functionality is available for PRO version.
This functionality is available for PRO version.
WordPress is the most popular CMS system, powering over 37% of all websites—a remarkable achievement. There’s no doubt that WordPress is a unique framework, offering a robust and flexible core structure alongside an intuitive and user-friendly administrator dashboard. One of its most compelling features is its extensive library of free plugins and themes, which provide incredible extensibility with just a few clicks.
However, this widespread popularity also attracts the attention of hackers, who are constantly searching for security vulnerabilities in WordPress sites. A single exploit can potentially compromise countless other sites using similar configurations and plugins, making security a critical concern for all WordPress users.
Table of Contents
What is a Firewall?
A firewall is a crucial security software that provides an essential layer of protection for your website. Acting as a rules-based filter, a firewall meticulously examines all incoming traffic to your site. It ensures that only legitimate and secure traffic reaches your server while blocking and logging any malicious attempts. By enforcing a set of predefined rules, firewalls can effectively identify and mitigate various cyber threats, including SQL injection, cross-site scripting (XSS), and distributed denial-of-service (DDoS) attacks.
Implementing a firewall is one of the most effective strategies for safeguarding your website against unauthorized access and potential data breaches. It not only prevents hackers from exploiting vulnerabilities but also helps in monitoring and analyzing traffic patterns, which can be invaluable for identifying potential security threats before they become serious issues. Modern firewalls offer advanced features such as real-time threat intelligence, automated responses to suspicious activities, and detailed logging for forensic analysis.
Why use a Firewall?
A firewall functions as a proactive rather than a reactive security solution, safeguarding your website by blocking malicious and malware attacks before they reach your server. This proactive approach significantly enhances security, preventing potential harm and damage to your site. By stopping threats at the outset, a firewall spares administrators from the incalculable losses that malware can cause, such as data breaches, downtime, and financial impacts. This preventive measure is crucial for maintaining the integrity and availability of your website, ensuring that both your data and your users remain secure.
What the WP Hide Firewall can do?
The firewall core is based on the renowned 8G Firewall solution, widely utilized across numerous servers. It features lightweight, well-optimized rewrite rules that provide robust server-level protection against various malicious requests, bad bots, automated attacks, spam, and other threats.
Some of the firewall features are:
- Security via simplicity
- Extensive firewall protection
- Fine-tuned to minimize false positives
- Lightweight (only 12KB!), modular, flexible and fast
- Completely plug-&-play with no configuration required
- Improves security, reduces server load, and conserves resources
- Git/SVN friendly (does not block svn/git files et al)
- Better bad bot detection
Types of attacks and threats the firewall can stop:
- Directory Traversal
- HTTP Response Splitting
- (XSS) Cross-Site Scripting
- Cache Poisoning
- Dual-Header Exploits
- SQL/PHP/Code Injection
- File Injection/Inclusion
- Null Byte Injection
- Plugins exploits such as revslider, timthumb, fckeditor
- Exploits such as c99shell, phpshell, remoteview, site copier
This comprehensive firewall solution offers exceptional security, ensuring your website is well-protected against a wide array of cyber threats.
How to activate the Firewall?
The feature works as an out-of-the-box solution, through the plugin Firewall interface the options need to be activated.
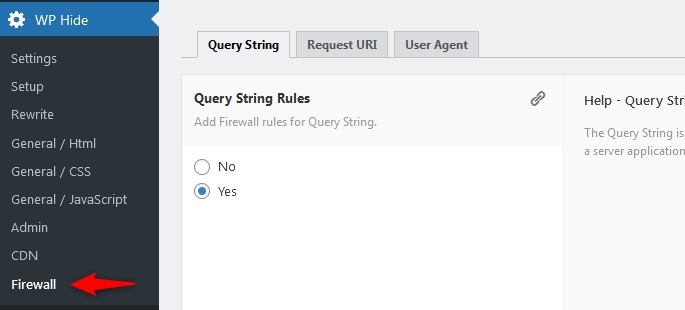
There is 3 types of firewall rules:
- Query String Rules
- Request URI Rules
- User Agent Rules
The Query String Firewall module, scans the portion of a URL where data is passed to a server application and/or back-end database.
The Request URI Rules, known as Uniform Resource Identifier, identify the resource upon which to apply the filters.
The User Agent rules, helps to block known malware bots and hack scanners.
The plugin interface includes a separate menu item for the firewall which can be used to control the active modules: