Harden Your Website using Security Headers
Any website is susceptible to remote attacks. Starting with the hosting server and its deployed applications, continuing with website CMS and deployed modules and extensions. Everything is potentially vulnerable.
The WordPress platform generally implies a high risk. The environment suit such as plugins and themes are found vulnerable all time. That creates security problems for everyone.
WP Hide is a great way to add another layer of security. Disguising everything on the site, the intruder is lost and unable to create a focused attack on a specific vulnerability.
On top of hiding, the plugin provides an easy way to manage the response Security Headers. The Security Headers are HTTP pieces of information, sent back to the user browser that heavily increases the overall security protection.
Table of Contents
What a Security Header is?
A Security header is an HTTP piece of information used by web applications to configure and increase the security aspects within user browsers. Based on the provided server directives ( the Security Headers ) a browser engine can make it harder to exploit client-side vulnerabilities such as Cross-Site Scripting, code injection or Clickjacking.
These headers are part of the HTTP response and are mainly a combination of key-value pairs.
Why use Security Headers?
Strengthening site security is the ultimate goal for everyone. Data breach happens all the time, many websites get hacked due to poorly code implementation, misconfiguration or lack of any type of protection. The Security Headers is a great way to greatly increase the overall site protection.
Which are the Security Headers?
There is a comprehensive list of headers that are indexed as security data. The WP Hide PRO can manage all of those headers:
- Cross-Origin-Embedder-Policy (COEP)
- Cross-Origin-Opener-Policy (COOP)
- Cross-Origin-Resource-Policy (CORP)
- Content-Security-Policy
- Content-Security-Policy-Report-Only
- Expect CT
- Permissions Policy ( replaced Feature Policy )
- Strict-Transport-Security (HSTS)
- X-Content-Type-Options
- X-Download-Options
- X-Frame-Options (XFO)
- X-Permitted-Cross-Domain-Policies
- X-XSS-Protection
How to implement the Security Headers using WP-Hide?
Depending on the server type ( e.g. Apache, Nginx ) a security header requires a special line on the system configuration. On Apache, it works with Header set while on Nginx it rely on the “add_header” directive. A header syntax is critical, as using the wrong format conclude to a whole site failure.
The WP Hide plugin eliminates this huge inconvenience. The Security Headers become easy to manage through a graphic interface, while the plugin core automatically creates the appropriate rewrite data and deploys on the server-side. Chose the required security headers and appropriate option makes the operation a click away:

Sample options interface for Cross-Origin-Embedder-Policy (COEP) security header:

Using the Check Headers interface, a feedback of active headers deployed on the site is returned. That ensures the headers are successfully deployed and active across the website. If apply, the module also outputs additional recommendations regarding specific headers to use.

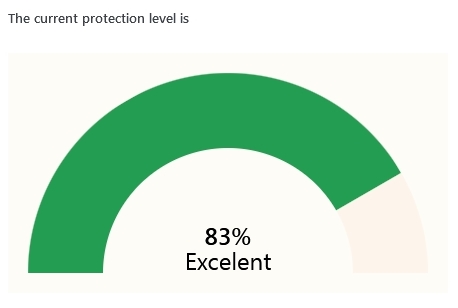
Based on the existing headers an algorithm calculates an estimated level of protection for the current site. This is a dynamic graph that changes accordingly to the new headers.

Recent Comments